Secure free spaces
IT security for operative technologies
Industrial manufacturing is based on the pillars of information and operational technology: in short, IT and OT. IT tasks include data processing and strategic planning of production on the company level, whereas OT handles specific control of the individual production lines and equipment. Both areas work towards the same company goals, though using essentially different working principles and procedures.
The digitalization trend of recent decades has brought with it not only great opportunities for productivity, but also the necessity of close cooperation between the two areas. This can be made more difficult with respect to IT security due to differing requirements of the two areas as well as different priorities and demands on processes or results.
The differences
| High data throughput, but chronology tolerance | Less data throughput, more real-time requirements (latency, jitter) |
| Safety is only indirectly affected by security incidents | Security incidents often with directly effects on safety |
| Useful life of standard components typ. 3-5 years | Useful life of machines and automation components typ. 10-20 years |
| Established security culture and experienced systems/IT personnel | First security experiences for automation pros |
| Confidentiality before availability | Availability before confidentiality |
| Frequent updates/patches Automated and native system component | Updates/patches often proprietary, manual and only with support from OEM |
With respect to security the differences between IT and OT can make cooperation more difficult.
Satisfying IT and OT
Therefore one key requirement for IT security products and services is not to impede productive and harmonious cooperation between IT and OT. Security measures and especially helpful in this relationship if they mean the least possible intervention in proven strategies and accustomed sequences on both sides and can meet both security and freedom requirements.
The core function of the W&T Microwall is just that: on one hand they protect individual network sectors in a targeted and controllable way, namely by using a whitelist to allow only individually selected and expressly desired communication. This works without affecting other network sectors. On the hand they open up protected free areas where production processes can continue unimpeded.
All Microwalls involve minimal integration effort since the desired filter rules are quickly created simply by specifying an IP address or port number. The Microwall Bridge even allows non-intervention integration into the IP configuration of the network sectors to be protected, making it ideal as an add-on and low-effort security enhancement.
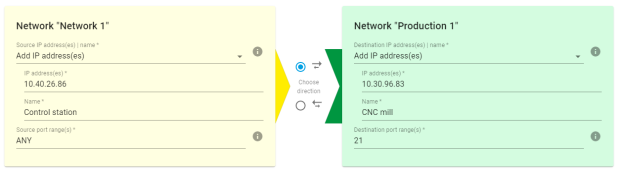
Simple integration and targeted protection on one hand, the needed free areas on the other - the W&T Microwalls meet the needs of IT and OT equally.
